Data erasure and data deletion may sound identical since they are both considered to be methods of “removing data.”
In layman's terms, "data deletion" can be thought of as emptying the Recycle Bin or Trash (on a Mac) or using the SHIFT + DEL command to relocate a file from a visible position on your system or external drive to an unidentified one. Similar to how information is removed from paper, "data erasure" can also mean erasing (or wiping) data so that it disappears from the storage medium and ends up somewhere else.
The truth is that data deletion and erasure are fundamentally distinct from one another in every way, from their intended use to how they work to the outcomes.
This blog clarifies the differences between the two by highlighting the critical distinctions between data deletion and data erasure. More importantly, it clarifies why understanding this distinction is vital in the age of data vulnerabilities and data protection legislation.
What is Data Erasure?
Data erasure, also known as data clearing, data wiping, or data destruction, is a software-based technique for overwriting data that aims to irreversibly overwrite all of the device's sectors with zeros and ones to completely erase all electronic data stored on a hard drive or other digital media. Data sanitization is accomplished by overwriting the data on the storage device to make it unrecoverable.
Software intended for data erasure should ideally:
- Enable selection of a particular standard based on particular demands.
- Check if the overwriting technique successfully removed the data from the entire device.
Necessary file deletion commands only eliminate direct pointers to the data disk sectors and leave room for data recovery using widely available software tools. Permanent data erasure goes beyond these limitations. Data erasure eliminates all data while leaving the disc functional instead of degaussing and physical destruction, which renders the storage media useless. Data erasure techniques may fail with new flash memory-based media implementations such as solid-state drives or USB flash drives, leaving residual data readable.
Characteristics of data erasure
Data erasure is software-based, unlike conventional data removal techniques, which can harm the storage media. It applies to isolated or unsupervised environments with both real and virtual devices.
A digital storage device is erased when its contents are entirely replaced with zeros and ones. The device's functioning is unaffected. However, all data is permanently lost.
A digital storage device is said to be erased when all its sectors are verifiably rewritten with zeros and ones. As long as the device is still functioning, this permanently deletes the data.
A specific file, folder, or location, such as a logical unit number (LUN), is verifiably rewritten during targeted sanitization. Non-targeted regions, meanwhile, are unchanged and continue to function. You can rest easy knowing that private information has been securely erased so that it cannot be recovered or accessed.
Data erasure software
A string of meaningless pseudo-random data is overwritten with all the data on a storage device, such as a hard disc drive (HDD), by data erasure software. A reliable erasure tool verifies deleted data to ensure it has been permanently destroyed.
In the event that an incorrect password is used for logging in, data erasure software can also remotely delete sensitive data. This method is frequently used in mobile devices to deter theft and protect user information in the event of device theft.
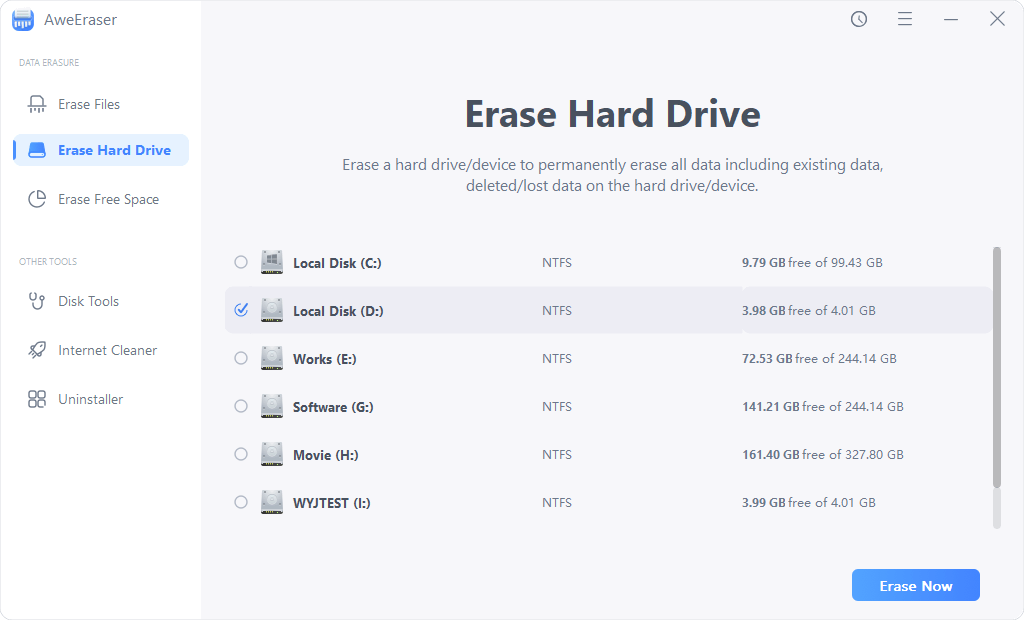
AweEraser is a powerful, easy-to-use and 100% safe data erasure program. It supports to permanently erase data from PC, Mac, HDD, SSD, USB flash drive, memory card, digital camera, etc.
Data Eraser - AweEraser
- Permanently shred files, wipe drive, erase deleted data, etc.
- Certified data erasure methods including HMG Infosec Standard 5, Peter Gutmann's, U.S. Army AR380-19, DoD 5220.22, etc.
- Once the data is erased, the data is gone forever, can’t be recovered by any method.
AweEraser offers three modes to help in permanently erasing data on Windows/Mac OS:
- Erase Files - permanently shred files and folders.
- Erase Hard Drive - erase all data on a hard drive.
- Erase Free Space - erase deleted/lost data on a hard drive.
Before you sell, donate or dispose of your device, you can run AweEraser to securely and permanently erase your sensitive data. Once the data is erased by AweEraser, the data is gone forever, can’t be recovered by any data recovery method.
Data erasure methods
The National Institute of Standards and Technology (NIST) lists the following methods for erasing data:
- Data erasure software overwrites obsolete or abandoned data with non-sensitive data (0’s and 1’s).
- Block erasure: To remove all data from a storage device, a data erasure tool targets all logical block addresses on the device, even those that aren't currently mapped to active addresses.
- For devices with built-in data encryption features, such Self-Encrypting Drives, the cryptographic wipe data erasure technique utilized (SEDs). The data on SEDs can become unrecoverable if a data erasure platform successfully destroys the key required to decode the data.
Why is data erasure necessary?
Data breaches are too common, and hackers constantly look for new ways to steal personally identifiable information (PII), intellectual property, and trade secrets. Because of the increased retention of sensitive data, accelerated technological advances, and the limited lifespan of IT assets, there is a need for permanent data erasure of electronic equipment when it is retired or reconditioned.
Several laws have been enacted in various industries in recent years to guide organizations on data protection and erasure to ensure regulatory compliance.
Although data erasure is not a new technique, it is gaining popularity due to the dangers associated with data security, privacy, and protection. Government agencies and businesses must impose updated protection measures for sensitive data management in light of significant data leakage scandals and cyberattacks, including ransomware assaults.
While managing a complex portfolio of IT assets, accurate erasure protects against data breaches, adhering to numerous data security standards, using resources best, and implementing green practices.
Erasing data provides tamper-proof erasure certifications to enterprises to ensure compliance with expanding data protection standards requiring data minimization, right to erasure, or right to deletion.
It also enables businesses to transition from less environmentally friendly data and equipment disposal techniques to more sustainable circular business models. Businesses can resell or repurpose devices with data erasure without fear of exposing sensitive data, significantly reducing electronic waste.
Challenges of data erasure
Data erasure could not be successful on flash-based media, including solid-state drives (SSDs) and USB flash drives.
These devices might have leftover data that the erasure algorithm cannot remove, and data can be recovered from the specific flash memory chips inside the device.
Only functional hard drives that write on all sectors can erode data by overwriting. While defective sectors are typically impossible for software to repair, they occasionally have data that can be restored.
On the other hand, damaged sectors may be invisible to the host system and thus to the erasing application. This issue is avoidable by encrypting the device before use. Malicious malware has the potential to interfere with software-driven data erasure.
Data erasure requires more time than other types of data sanitization. Furthermore, data erasure necessitates the development of policies and practices for all data storage devices.
Take no chances.
Adopt Secure Data Erasure to Get Rid of Unwanted Data
Data erasure is one of the safest and most effective techniques to eliminate unnecessary data. As was previously said, the method relies on overwriting the addressable memory locations with binary patterns to obliterate the data, making it impossible to recover using any data recovery method or tool.